Citrix Netscaler Azure VM – Add and Bind Intermediate Certificates
Ive been working on Azure quite a bit recently and part of a project was to roll out Citrix Xen App 7.1. This was to be presented both internally and externally. To provide users with external access I installed and configured the Netscaler Azure VMX from the Microsoft marketplace. It was quite fiddly to get going to I plan on popping a few articles up for the more fiddly bits.
This particular article is about uploading and binding your certificates to the external interface and if required linking the intermediate certificate to your certificate.
Upload Certificates to the Netscaler
Nice and simple, follow the below steps:
- Navigate to Traffic Management > SSL > SSL Certificate > Server Certificates
- Select Install
- Browse to your certifcate
- Select upload
- Wait until Certificate is uploaded in bottom right corner ( you may need to select refresh)
- Repeat for all certs (intermediate if required)
Linking Intermediate Certificates on the Netscaler
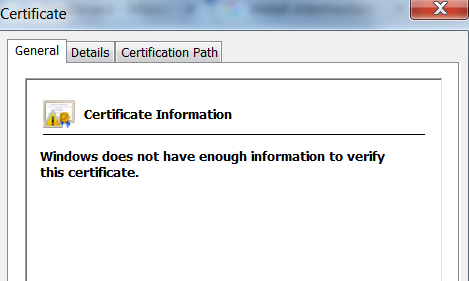
Again a simple process but if you do not do it then you will see the following errors in your browser when users attempt to connect to the external URL.
If you delve deeper the reason is because the certs are not linked and you get the error “windows does not have enough information to validate the certificate”
To resolve these we can link the certificates with the following process:
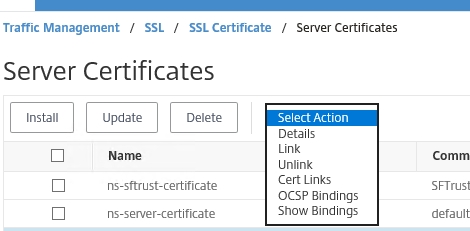
- Navigate to Traffic Management > SSL > SSL Certificate > Server Certificates
- Select both your web cert and the intermediate certificate
- Select actions > Link
Binding Certificates on the Netscaler
Now that we have all our certificates in place on the Netscaler we need to actually bind them to the services we are providing. In my case im binding to the externally accessible interface (port 443 ). Follow the below procedure:
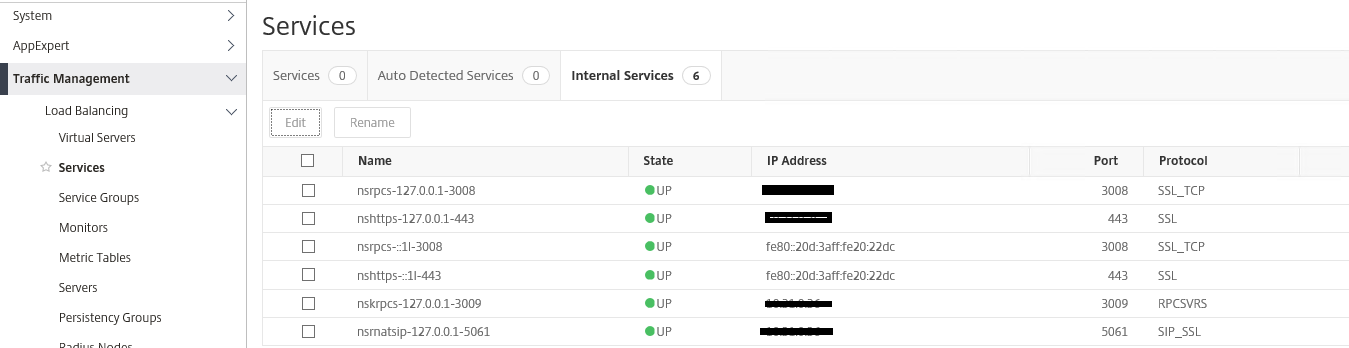
- Navigate to Traffic Management > Services > Internal Services
- Select the service that is using 443
- Select edit
- Select the web certificate we have installed and binded to the intermediate (if required)
You will now need to reboot the netscaler, once done all your certificates should be up and running
Tags: netscaler